Web-AI Tool Usage: Safe by Default
Let employees use ChatGPT, Gemini, Claude, and other web AI tools without risking data leakage, prompt attacks, or policy violations. Meshulash enforces guardrails on the endpoint so work keeps moving and sensitive data stays inside.

Solve Real Problems
Web AI tools unlock speed and productivity, but uncontrolled use exposes sensitive data, violates compliance requirements, and creates audit gaps. Meshulash lets teams gain the benefits while eliminating the risks through endpoint guardrails, data redaction, and policy enforcement.
Risks of Using Web AI at Work
What can go wrong without guardrails
Data Leakage via Prompts
Employees paste PII and IP into chats; info may be stored or processed externally, risking leaks and competitive loss.
Hallucinations & Bad Decisions
Confident-but-wrong outputs lead to faulty emails, code, pricing, or legal claims, causing brand damage and rework costs.
Shadow AI & Cost Sprawl
Uncontrolled tool use, no audit trails, surprise bills, and inconsistent policies across teams go unmanaged.
Unlawful Processing of Personal Data
Prompts contain PII without a valid legal basis, breaching privacy laws like Israel Amendment 13 and GDPR.
Cross-Border Data Transfers
Sending data to models hosted abroad without required safeguards or Data Processing Agreements violates privacy frameworks.
Records, Retention & E-Discovery Gaps
No logs or DPAs prevent honoring access/erasure requests and proving compliance after incidents.
High‑Impact Use Cases
What teams achieve with Web AI
Sales Emails That Convert
Draft personalized outreach in minutes using real context: higher response rates with less manual effort.
Case-Specific Support Replies
Summarize tickets and propose fixes using case details for faster first response and resolution time.
Spreadsheet Cleanup & Analysis
Transform messy tables, extract insights, and generate summaries, saving hours on reporting and QA.

Policy, HR, and Legal Drafts
Create first drafts and translations with consistent tone and quicker review cycles across teams.
Research & Meeting Summaries
Condense long docs and calls into action items for better follow-through and alignment.
Team-Wide Productivity Kits
Share standard prompts and templates by department for repeatable results at scale.
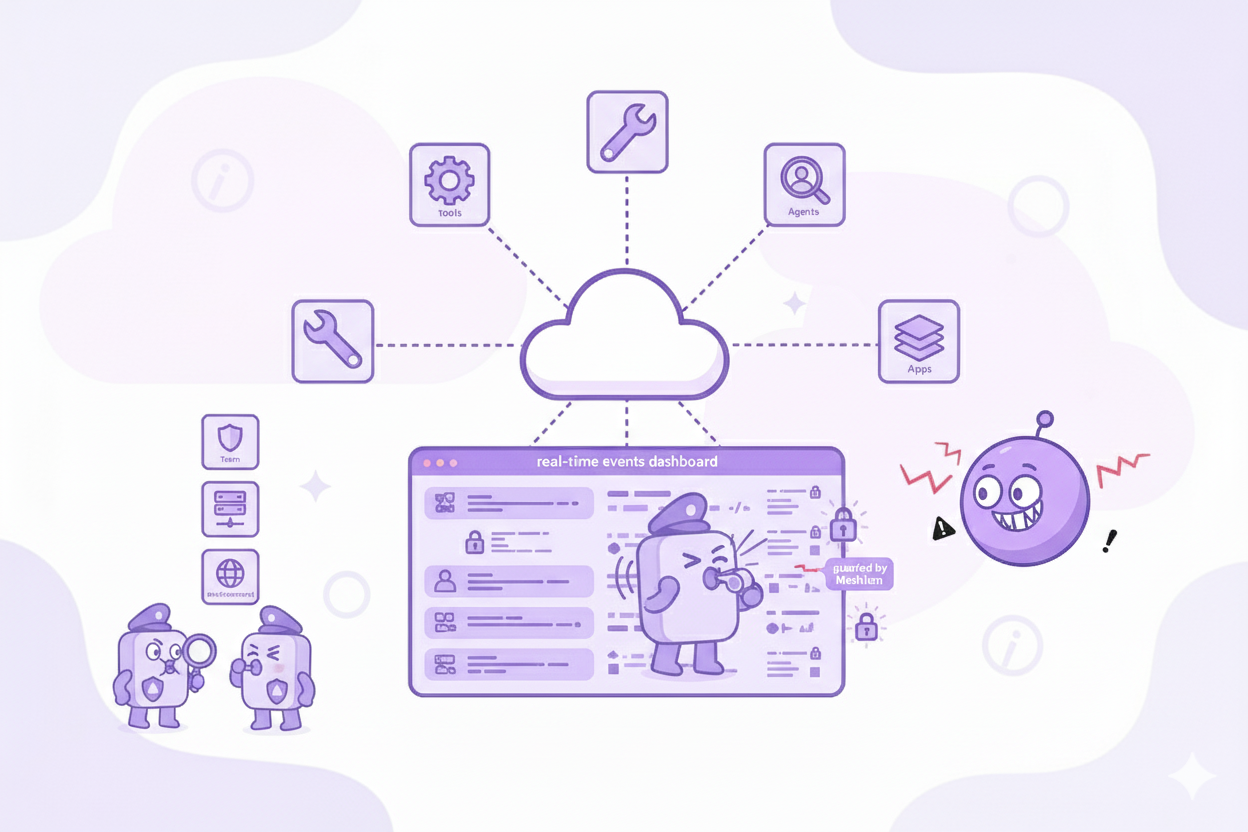
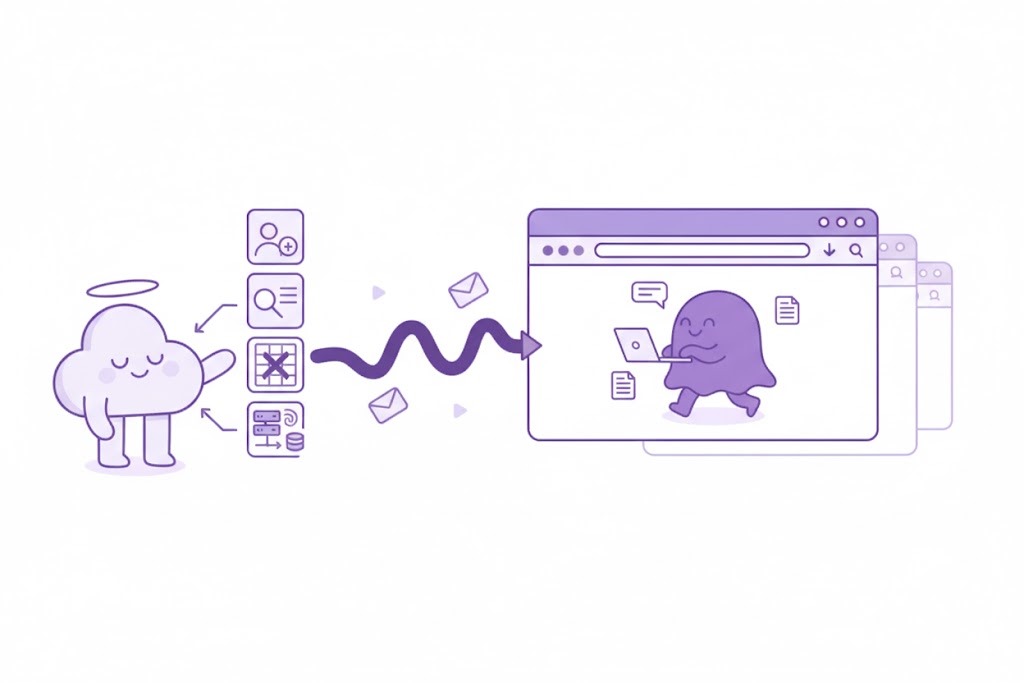
Benefits Without Risk: Guardrails Where Work Happens
Employees keep their tools and speed while sensitive data stays in-bounds. Prompts and files are checked on the endpoint, risky instructions are stopped, and traffic stays on approved routes so teams get the benefits without the usual risks.
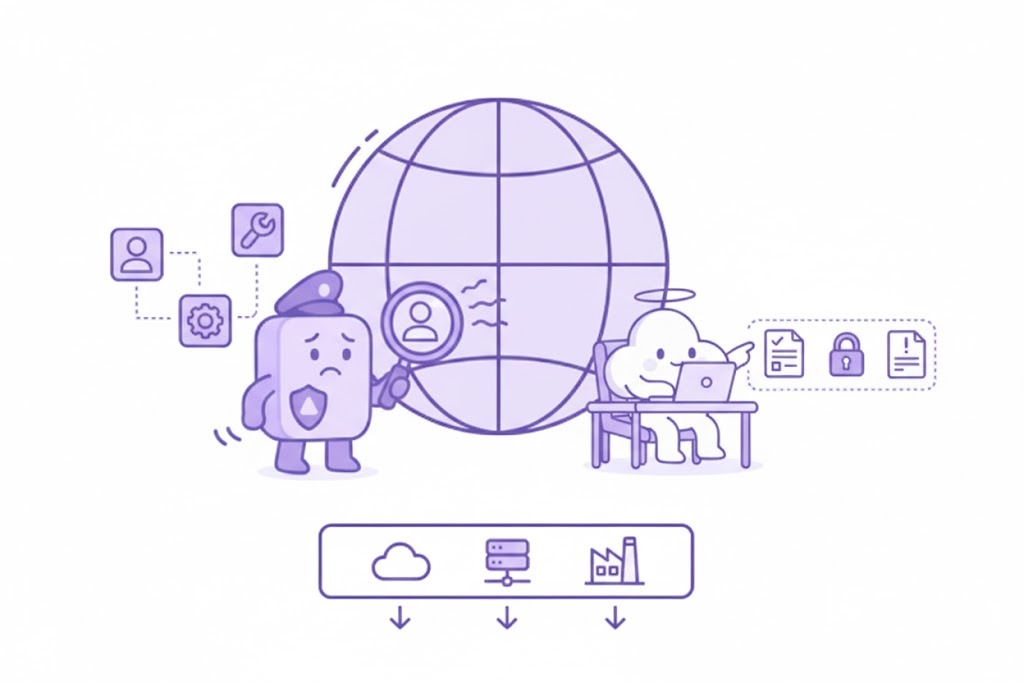
Benefits Without Risk: Visibility & Control
See who used what, when, and for what without blocking productivity. Tune rules by team, approve new tools cleanly, and keep an auditable trail for compliance in cloud, hybrid, or on-prem environments.
Frequently Asked Questions
Quick answers to common questions
No. Meshulash runs quietly on the endpoint. Prompts and files are checked locally; employees keep the same web AI tools and flow.
Any browser-based AI chat or assistant: ChatGPT, Gemini, Claude, and internal portals. If it runs in the browser, Meshulash can protect it.
Meshulash discovers usage as it happens, surfacing new tools and sessions. You can allow, monitor, or block globally or per department.
PII (names, emails, phone numbers), secrets (keys, tokens), and IP (code fragments, architecture identifiers), plus custom data classes you define. Redaction occurs on-device before sending.
Yes. Files and screenshots are scanned locally; risky content is blocked or redacted per policy before leaving the browser.
Meshulash analyzes intent and context to detect manipulation or privilege-escalation attempts and enforces your chosen action (block, warn, log) before execution.
Sensitive content is not stored. Meshulash retains only minimal metadata needed for visibility and incident response, according to your retention settings.
Yes. Apply different actions and thresholds by department, group, or geography to match process and regulatory needs.
Yes. Use SSO for identity and stream events to SIEM/SOAR for correlation and response.
Yes. Meshulash supports cloud, hybrid, and on-prem deployments with the same endpoint guardrails and governance model.
