Internal Access & Jailbreak: Enforce Boundaries for AI
Internal assistants access CRMs, DBs, and APIs, but without guardrails, jailbreaks and prompt injections trigger unauthorized actions and data leaks. Meshulash enforces access boundaries pre-execution so your assistants help, not harm.

Solve Real Problems
AI inside your network accelerates support, operations, and automation, but uncontrolled access creates privilege escalation, data exfiltration, and compliance gaps. Meshulash gives you a single control plane to define what assistants may access, enforce scope boundaries, and audit every action.
Risks of Internal AI Access
What can go wrong without guardrails
Prompt Injection & Jailbreaks
Malicious instructions in chat or logs cause agents to bypass intended scope and trigger unauthorized actions.
Privilege Escalation
Agents escalate permissions to access restricted data, perform admin actions, or call high-risk APIs without policy approval.
Unscoped Data Access & Leakage
Agents query databases, customer records, or internal repos with no field-level or row-level restrictions, exfiltrating sensitive data.
Unauthorized API Calls
Assistants call external or internal APIs without validation, triggering unintended transfers, deletions, or state changes.
Insider Threat & Audit Gaps
No logs of AI actions make it impossible to detect insider abuse or prove compliance after a breach.
Shadow Assistants & Sprawl
Unapproved or misconfigured internal agents operate without oversight, creating blind spots and inconsistent risk posture.
High-Impact Use Cases
What teams achieve with secure internal AI
AI-Powered Customer Support with Safe RAG
Assistants answer from approved knowledge bases and case histories without access to unrestricted customer data or adjacent systems.

Privilege Escalation Prevention
Agents attempt to access sensitive salary or compliance data via connectors, but policy blocks the request pre-execution and logs it for audit.

Secure Ticket Automation & CRM Updates
Workflows auto-triage support tickets, create runbooks, and update CRM fields using approved APIs and predefined actions only.
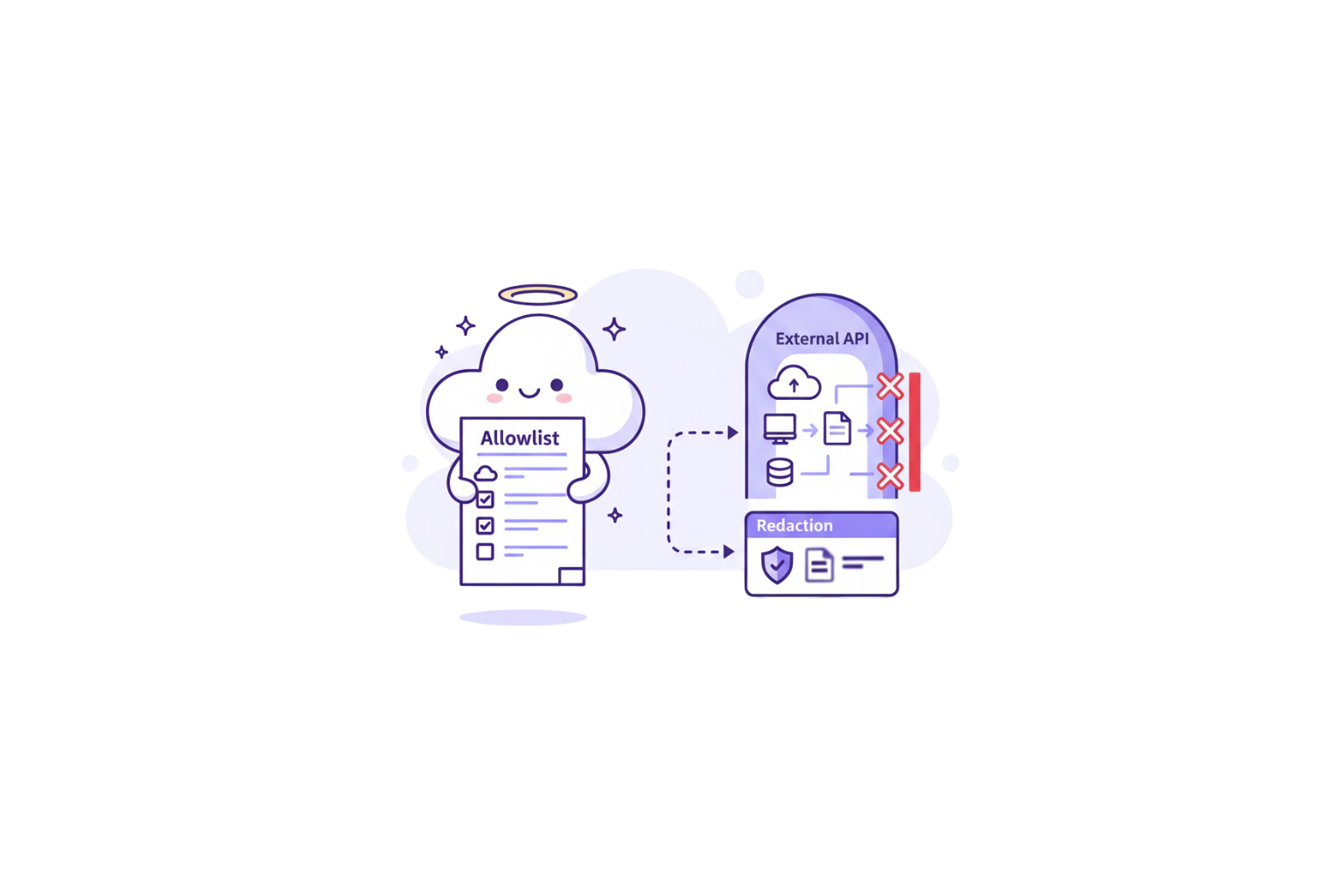
Controlled External API Access
When workflows need external APIs, policy enforces allowlists and redacts regulated fields, keeping sensitive data in-network.

Fast Incident Investigation & Response
Every denied request, API call, and policy hit is logged with user, time, and context, enabling rapid incident triage and root cause analysis.

Cross-Team Policy Consistency
HR, Finance, Support, and Operations teams each get tailored scope rules but follow the same enforcement model and audit trail.
Benefits Without Risk: Access Boundaries Enforced Pre-Execution
Assistants keep their speed and automation reach while staying within defined access boundaries. Policy is enforced before actions execute, risky requests are blocked or redacted, and every invocation is logged so teams move fast and safely.

Benefits Without Risk: Visibility & Audit
See which assistant ran, what action it triggered, and whether policy approved or blocked it. Adjust rules per team, approve new connectors cleanly, and maintain a full audit trail for compliance across dev, staging, and production.

Frequently Asked Questions
Quick answers to common questions
Prompt injections, jailbreaks, indirect manipulations, off-scope data retrieval, access to disallowed tools/resources, and external egress not on the allowlist before execution.
No. We focus on inputs, invocations, source/scope control, and egress, not output rewriting.
It augments IAM with AI-aware controls: per-tool/per-resource permissions at the invocation layer (MCP IAM) tied to SSO identity and environment.
By default, no. They route through approved in-network endpoints (gateway/security server). External calls occur only if your policy explicitly allows them.
CASB/DSPM govern apps and data posture. Meshulash governs AI interactions—understanding context and intent and enforcing policies at the exact point where assistants access data and tools.
Yes. Apply the same API/SDK + security server policies to internal bots and external applications for consistent boundaries and auditability.
No. Sensitive fragments are redacted; we retain only minimal metadata necessary for visibility and incident response per your retention settings.
