IDE & Development Agents: Control Without Friction
AI speeds up development, but uncontrolled code assistants and agents leak secrets, expose IP, and trigger unauthorized API calls. Meshulash lets teams ship faster with guardrails that keep sensitive code and credentials local and in-network.

Solve Real Problems
AI in development (IDEs, agents, workflows, MCPs) accelerates shipping, but uncontrolled use leaks secrets, exposes IP, triggers unauthorized API calls, and breaks compliance. Meshulash lets teams gain speed while eliminating risks through local masking, policy enforcement, and in-network routing.
Risks of AI in Development
What can go wrong without guardrails
Secret Leakage in Prompts
API keys, credentials, and tokens pasted into IDEs or agents end up in logs, training data, or external models.
Source Code & IP Exposure
Code snippets, architectures, and proprietary logic pasted for AI assistance leak to third parties or are retained by external services.
Uncontrolled API & Resource Access
Agents call APIs, DBs, or internal tools without scope limits, triggering unauthorized changes or data access.
Prompt Injection & Jailbreaks
Malicious inputs in code comments or configs cause agents to bypass security controls or execute unintended actions.
Shadow AI Sprawl
Unapproved IDE assistants and agents run unchecked, creating blind spots and inconsistent security posture.
Audit & Compliance Failures
No logs of AI invocations, data flows, or access make incident response and regulatory compliance impossible.
High-Impact Use Cases
What teams achieve with secure AI development
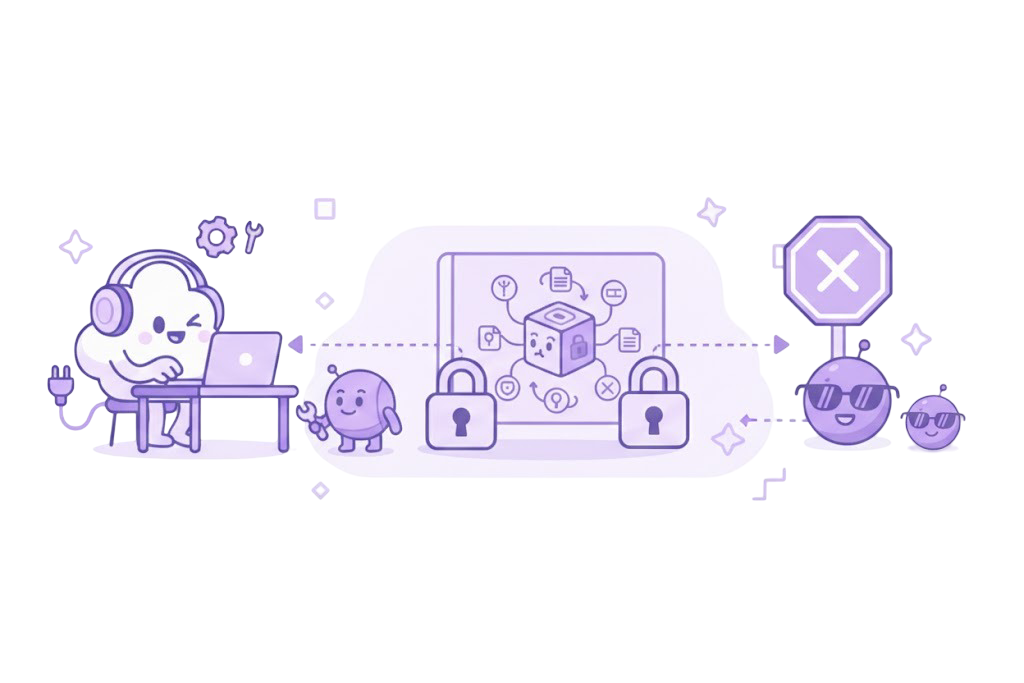
Secure Code Completion & Coding Assistants
Engineers use Copilot, Claude, or other IDE assistants to speed up development while secrets and IP stay local.
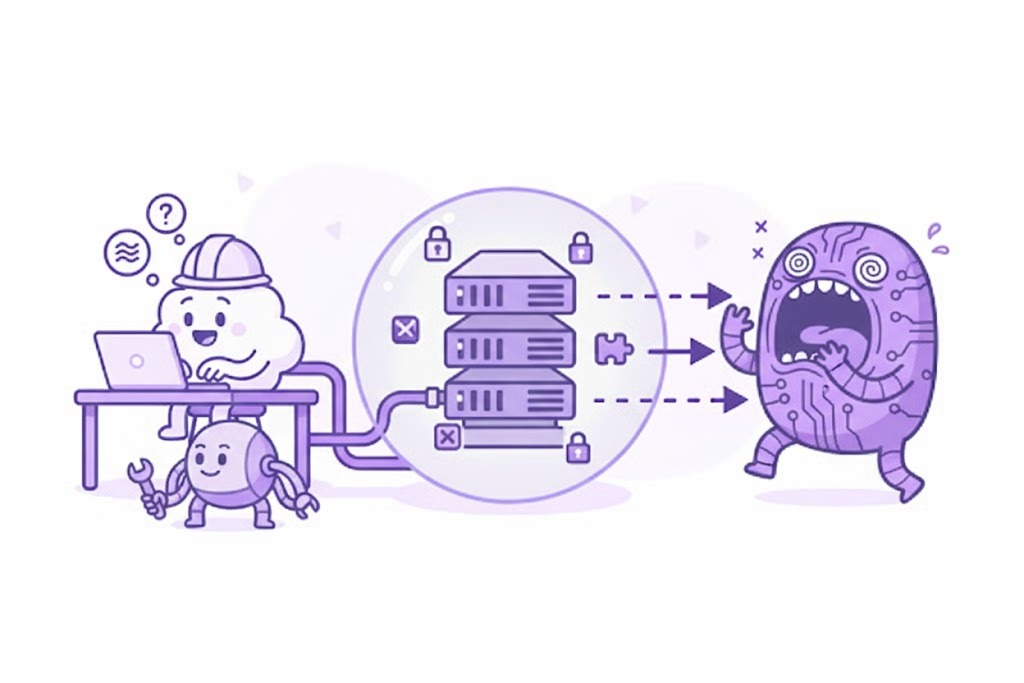
AI-Powered Code Review & RAG
Agents analyze code and pull down docs from approved internal sources, suggesting fixes and best practices without leaking proprietary context.

Automated Testing & QA with Guardrails
AI agents generate test cases and validate deployments using approved APIs and resources, with every call logged and audited.
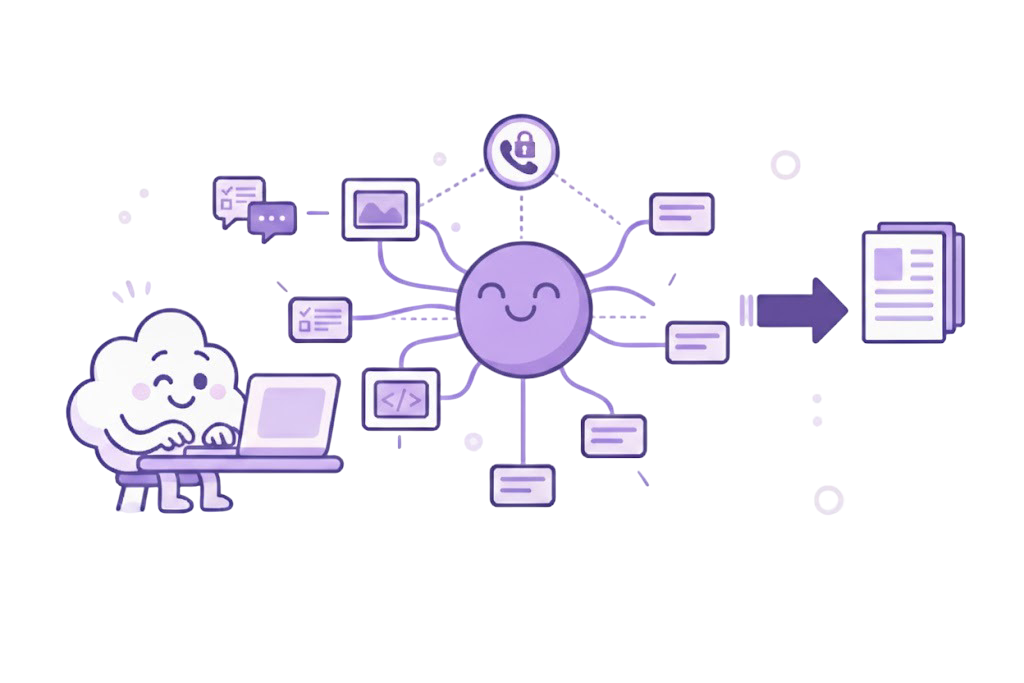
Ticket Triage & DevOps Automation
Workflows and agents auto-triage issues, create runbooks, and trigger deployments using in-network APIs while redacting sensitive fields.
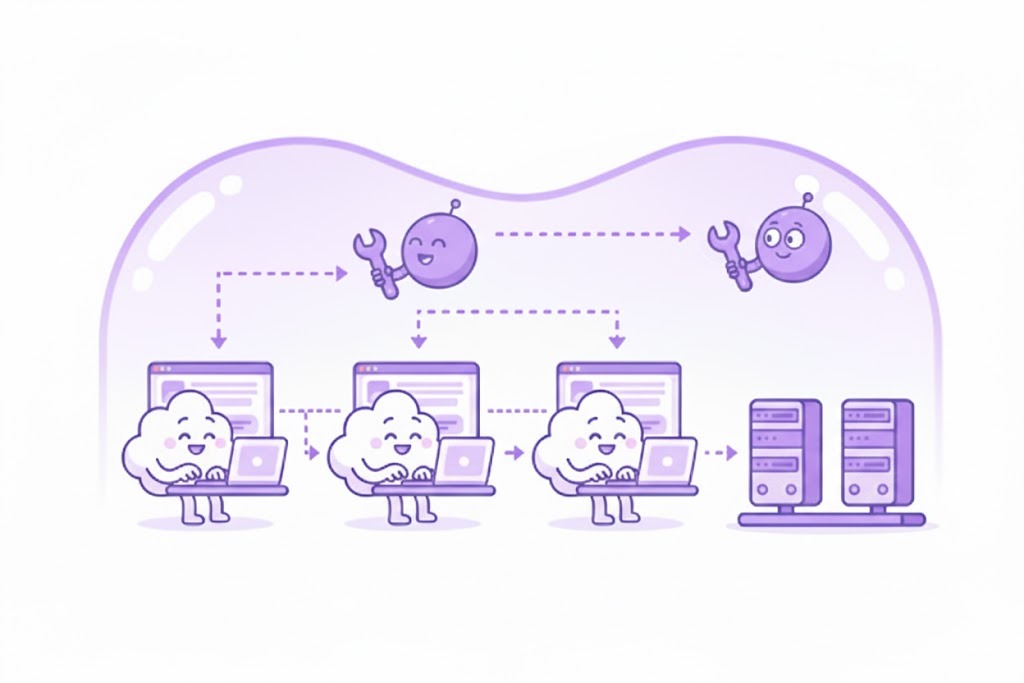
Standardized MCP & Agent Ecosystem
Teams use approved MCP servers and AI agents consistently, reducing onboarding time and improving predictability across projects.
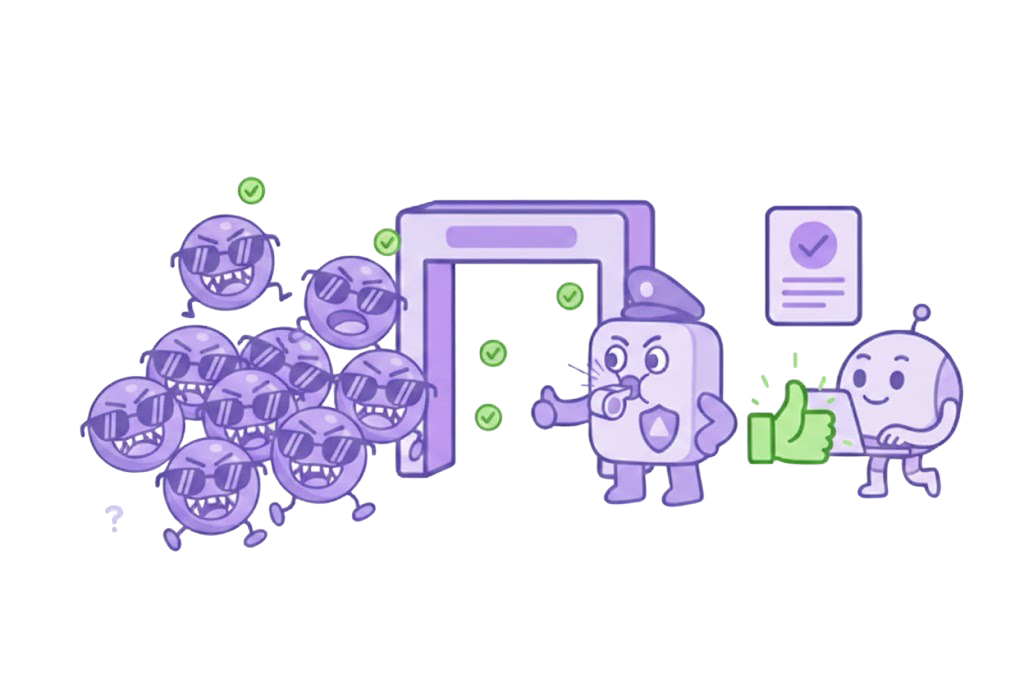
Managed Shadow AI Discovery
Discover new AI tools and assistants as they appear, approve safe ones quickly, and manage costs and compliance across teams.
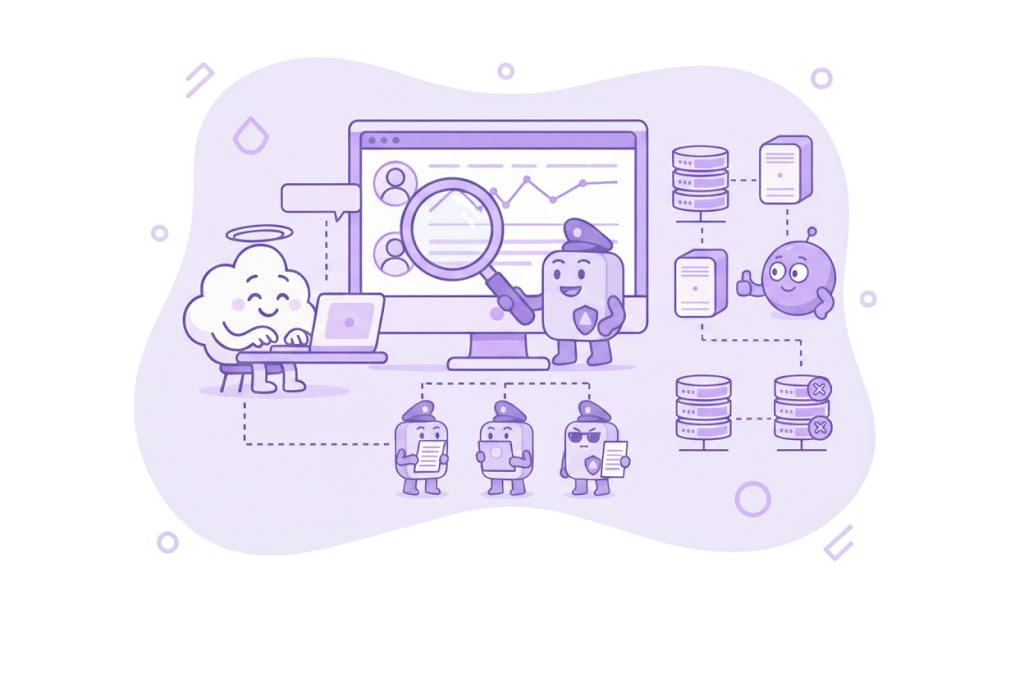
Compliance & Audit-Ready Workflows
Every AI invocation across CI/CD, testing, and DevOps is logged with user, time, and action, making compliance and incident response straightforward.
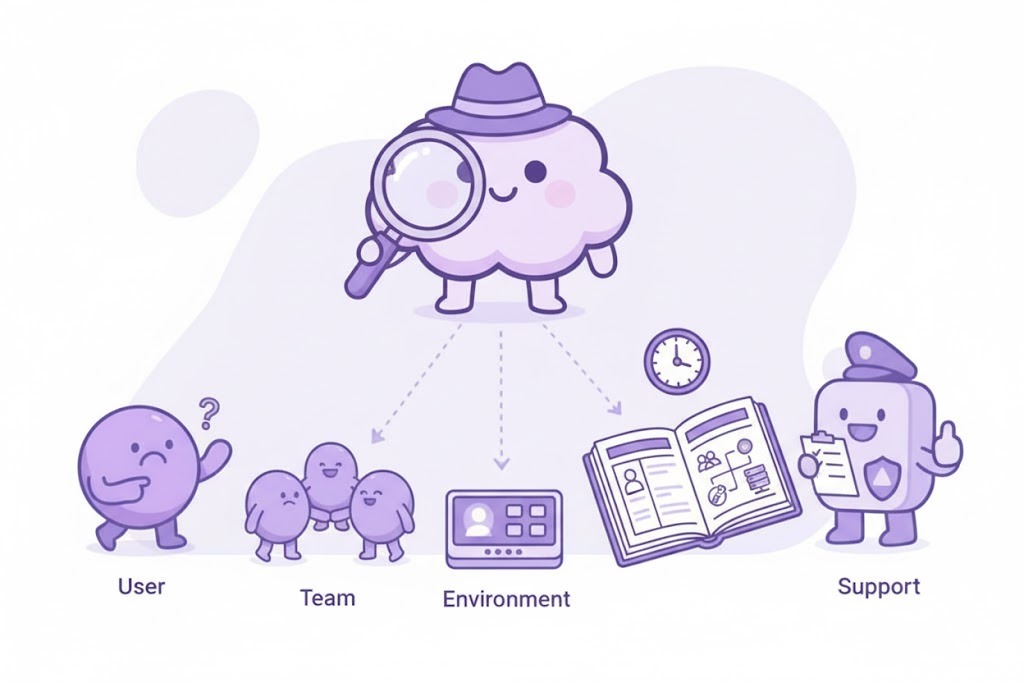
Cross-Team Policy Consistency
Frontend, backend, and infrastructure teams follow the same AI security policies, eliminating ad-hoc exceptions and reducing support burden.
Benefits Without Risk: Guardrails at the Point of Development
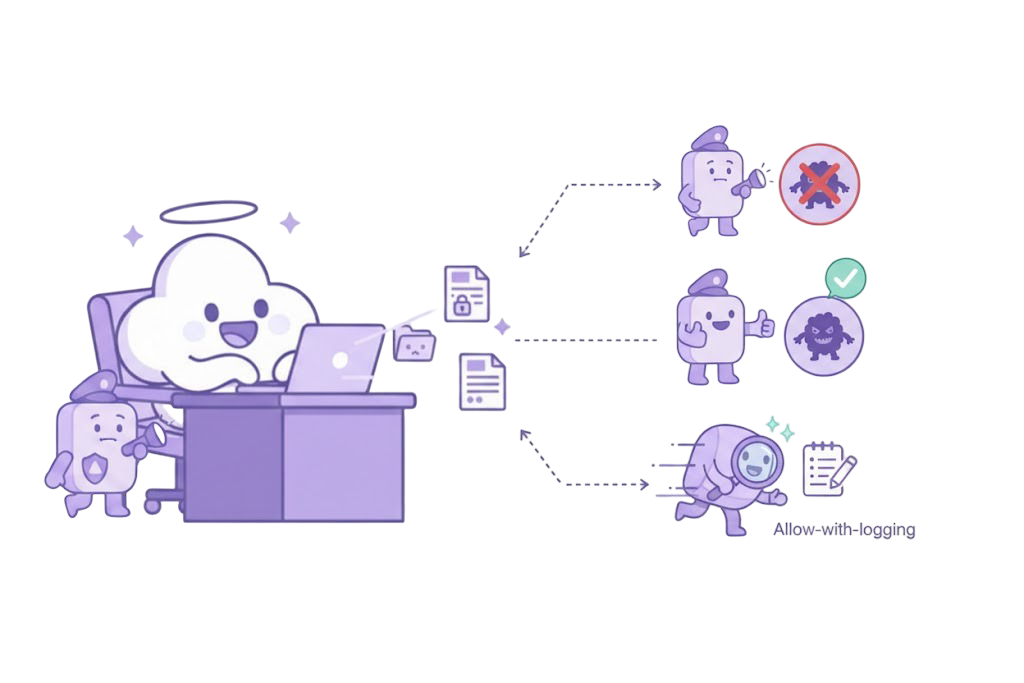
Engineers keep their tools and speed while secrets and IP stay protected. Prompts and code are checked locally, malicious instructions are blocked, and traffic stays in-network so teams ship faster without exposing sensitive assets.

Benefits Without Risk: Visibility & Compliance
See which assistants and tools are used, by whom, and for what. Tune policies per team, approve new tools cleanly, and maintain an auditable trail across dev/staging/prod for compliance and incident response.
Frequently Asked Questions
Quick answers to common questions
Yes, they leave the workstation, but Meshulash routes them only to approved in-network endpoints by default. They do not traverse the public internet unless you explicitly allow it in policy.
No. Meshulash focuses on prompts, tool invocations, and data leaving the IDE. Sensitive fragments are masked locally; only minimal metadata is retained for visibility and incident response.
Yes. Meshulash enforces source allowlists and scope policies for RAG, strips PII/IP at request time, and blocks off-scope collections so agents retrieve from approved, in-network sources with citations and auditability.
Requests pass through the security server, which evaluates context and intent and applies policy (block/redact/allow) before actions execute or data leaves your network.
Yes. The MCP Gateway lets admins choose allowed servers, tools, and resource scopes; every invocation is tied to identity and environment for audit.
No. We don't modify model outputs. We control inputs, govern allowed assistants/tools, and log usage for auditability.
Yes. Policies can vary by team/service and environment, with actions Allow / Block / Warn / Log and lightweight approvals for new tools.
Yes. Apply the same policy model via the API/SDK + security server to internal bots and external applications.
Yes. Meshulash supports cloud, hybrid, and on-prem deployments with the same policy model and event feeds to your SIEM/SOAR while keeping traffic inside your network by default.
