Enable your organization to use AI, no matter what.
Stay ahead of regulations and competitors by harnessing the power of AI in a secure, monitored, governed way.
AI is awesome. With great power comes great responsibility.
Safeguarding your data and closing security gaps is no longer optional.
80%
of enterprises face AI attacks, making it the #1 risk for big businesses.
55%
of employees use unapproved GenAI tools at work.
48%
of employees pasted non‑public company info into GenAI.
Understand and Mitigate AI Risks
Prompt injection, leakage, compliance drift, and hallucinations are real. See them clearly and plan your defenses.
Data Leakage
Sensitive docs, client data, credentials, and code leak to external AI.
Prompt Manipulation
Malicious prompts extract secrets or trigger unintended actions.

Regulatory Gaps
Hard to prove GDPR/ISO/SOC 2/HIPAA compliance without controls.
MCP Access
Connectors/APIs/MCP expand access; weak IAM widens your attack surface.
Why Existing DSPM and CASB Tools Fall Short
Traditional Data Security Posture Management (DSPM) and Cloud Access Security Broker (CASB) solutions were built for structured systems and predictable data flows. They can classify files, monitor APIs, and enforce access controls. But they cannot interpret the intent or context of AI interactions.
Generative AI introduces semantic risk: a harmless-looking prompt can expose sensitive logic, intellectual property, or client information in natural language form. Since DSPM and CASB lack real-time language understanding, they cannot detect such exposures or policy violations as they occur.
Meshulash AIM addresses this gap with adaptive, semantic enforcement at the point of interaction, understanding not just what data is being shared, but why and how it is being used.
Get visibility to all your AI usage and secure it with Meshulash's cross-team features
Meshulash AIM addresses a broad spectrum of enterprise AI security and governance scenarios.
CISO-First Control
CISOs are under pressure to control AI usage while keeping the business moving. Blocking tools is fast, but it kills innovation.
Instead of spending hours handling employee complaints or constantly configuring what to block and what to allow, Meshulash AIM removes that overhead entirely. It gives CISOs full control and clarity without the endless maintenance, saving time while keeping teams productive and satisfied.

Deployment Options
Every organization has different security and infrastructure needs—Meshulash AIM adapts to all of them.

Full SaaS (Remote)
Both the application/business layer and the security/enforcement layer run on Meshulash’s servers. Fastest time to value with no infrastructure to manage.
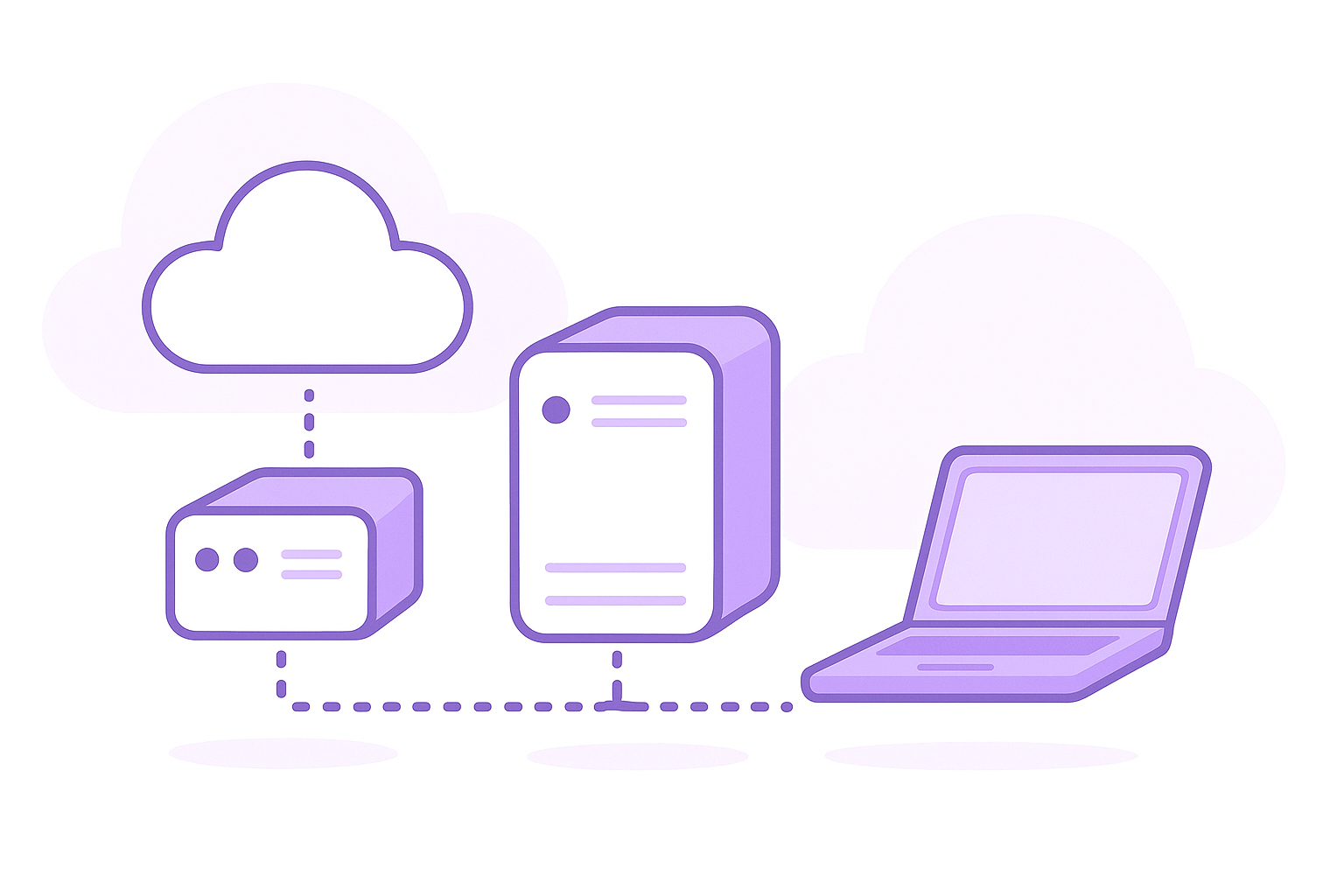
Hybrid (Customer‑Deployed Security)
Meshulash hosts the application/business layers. You deploy the security/enforcement layer inside your environment, keeping redaction and policy enforcement local while Meshulash operates the control plane.

Fully On‑Premises
All layers, dashboard, control plane, databases, security server, and enforcement nodes run entirely within your environment.
Across all models, Meshulash ensures that data is redacted before transmission, encrypted in transit and at rest, and that administrative control remains centralized or local depending on how you deploy.






